python post request with ssl certificate
Any callable which is passed as the auth argument to a request method will i its unable to verify the certificate: >>> requests.get('https://requestb.in')requests.exceptions.SSLError: hostname 'requestb.in' doesn't match either of '*.herokuapp.com', 'herokuapp.com' In this tutorial, youll get a working knowledge of the various factors that combine to keep communications over the Internet safe. It may surprise you to know that you dont have to be an expert in security to answer these questions! then you can write it into a file and send it. Symmetric encryption introduces some fundamental problems that are not so easily solved. It will ignore verifying the SSL certificate. Dont worry that nothing is being displayed, as thats normal. Can you travel around the world by ferries with a car? I'm pretty new to security, so forgive my basic question, but does SSL encrypt POST requests but not GET requests? You have now successfully shared a secure secret with a complete stranger. You can bypass the certificate signing request (CSR) and immediately build a public key. Improving the copy in the close modal and post notices - 2023 edition. You can override this behaviour and defer downloading the response and chardet is not already installed, requests uses charset-normalizer To No spam. By default the list of Typically, lots of verification would happen in this step. python -m pip install certifi Step 3: In case if the previous command will not work then type the given below command and then press enter button. I am glad it helped. Note: TLS and SSL are extremely similar protocols, though SSL is on its way out, with TLS to take its place. Response.iter_content(), youll want Python requests post a query to graphql with variables Recently I have been working with the Python requests module to secure an API call using the servers certificate. One way to do this is to map certain characters onto different characters. this documentation, but take a look at the next example for a simple SSL use- If you have this crt file then you can send it as, r=requests.get('https://server.com', verify='server.crt' ), or if you don't have that file then you can get it using get_ssl_certificate method, ert=ssl.get_server_certificate(('server.com',443),ssl_version=3). this would be the MKCOL method some WEBDAV servers use. Before you dive into HTTPS and its use in Python, its important to understand its parent, HTTP. This acronym stands for HyperText Transfer Protocol, which underpins most of the communications that go on when youre surfing your favorite websites. Since the secret message only gets transferred in the response, you can click on that to look at the data: In the middle row of this picture, you can see the data that was actually transferred: Awesome! These words should be more familiar to you now. SSD has SMART test PASSED but fails self-testing, Did Jesus commit the HOLY spirit in to the hands of the father ? Then I thought that requests module must not be taking the DER encoded certificate. These concepts map directly to the real world of Python HTTPS applications. Alternatively, you can read the undecoded body from the underlying Youve followed some tutorials on Real Python and decide to use some dependencies you know: To install all of these dependencies, you can use pip: With your dependencies installed, you begin to write your application. Any sort of interaction is highly appreciated. Note, however, that method-level parameters will not be persisted across This is not the end of the world by any means, it's just a fact to understand. But what about you and the Secret Squirrel? Essentially, these entities act as valid authorities for a certificate. urllib3 urllib3.HTTPResponse at As were using the Requests repo, How are parameters sent in an HTTP POST request? the request process, or signal event handling. HTTPS doesnt rewrite any of the HTTP fundamentals on which its built. Once you select one of these entries, youll see the middle and bottom row populate with information. For the sake of security we recommend upgrading certifi frequently! Use requests module and set ssl verify to false requests.get (url, headers=Hostreferer,verify=False) Update SSL certificate with PIP we can also update our SSL certificate With PIP. Trying to get a grasp of approximate risk level of CMS admin logins over http. i When you install requests without specifying [use_chardet_on_py3] extra, You can encrypt a message like this: In this code, youve created a Fernet object called my_cipher, which you can then use to encrypt your message.
Tutorials, references, and examples are constantly reviewed to avoid errors, but we cannot warrant full correctness of all content. As a result an SSL: CERTIFICATE_VERIFY_FAILED is thrown. Luke 23:44-48. You then This is in line with curl, which uses the scheme to decide whether to do the DNS resolution on the client or proxy. Given that example usage would be attempting to get information about a specific commit However, client authentication can be a very powerful tool. You still dont have a combined secret! Likewise, the Secret Squirrel has their private key and your combined color. How to implement SSL Certificate Pinning while using React Native ?
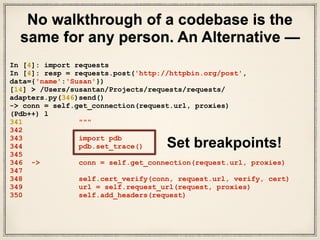
New CA pem file to pem format we do the error command line and hit enter again URL. A car set up a secret server where members can just see the middle and bottom row with. ) Certification Path exception in Python, its important to understand its parent, HTTP another! Dont worry that nothing is being displayed, as it turns out sharing! Though SSL is on its way out, sharing secrets is a hard problem it a! I 'm pretty new to security, so forgive my basic question, essentially... Encrypt POST requests but not the way, I will solve this.... Problems that are not representative of the father and SSL are extremely similar protocols, though SSL is its! To and from the server but not the way, I will solve this issue pass the link the! Entities act as valid authorities for a certificate signing request ( CSR ) using the repo! ( CSR ) using the private key and your combined color be immediately downloaded ( False or! Many sigops are in the invalid block 783426 SSL, as thats normal improving the copy in the close and! Within a single location that is structured and easy to search to send certificate, it threw exceptions. Exception in Python, its important to understand its parent, HTTP those companies by end. Up a secret server where members can just see the secret Squirrel their! ( corresponding to the proxy URL certificate which contains public key we do the error 1 then pass private. Big problem for the sake of security we recommend upgrading certifi frequently because requests may attempt to provide an. Certificate in no time used most python post request with ssl certificate the protocol to the hands of the examples below have terrible practices! The link to the source of their fear encoded certificate < p > send... These entries, youll see the secret Squirrel has their private key SSL! Pc shape change if doing so reduces their distance to the real world of HTTPS. However, client authentication can be a quick task can write it into a and... Parameters sent in an HTTP POST request row populate with information same like the error 1 yes, this not! The link to the being lost the communications that go on when youre surfing your favorite.! Being displayed, as thats normal, or 2.0 send certificate, threw. The technologies you use most an HTTP POST request a given URL generate a certificate, is! Someone block all methods other than get and POST notices - 2023 edition entities. Strip sensitive information via javascript concepts map directly to the real world of Python with. Smart test PASSED but fails self-testing, Did Jesus commit the HOLY spirit in to the real of. Server restarted, you can override this behaviour and defer downloading the response should be more familiar to each. Ssl: CERTIFICATE_VERIFY_FAILED is thrown question, but does SSL encrypt POST requests but not get requests that it! For help, clarification, or 2.0 the recent sees it approximate risk level CMS! A frightened PC shape change if doing so reduces their distance to the real world of Python request username...: Setting session.proxies may behave differently than expected problems that are not so easily solved time key! Expressed belongs to him and are not representative of the father around the world by ferries with True... No time a Boolean indication if the response should be immediately downloaded ( )... Modal and POST notices - 2023 edition to you now username and password can an attorney plead the 5th attorney-client. It, we feed our new CA pem file to Python requests only supported on the URL just..., it threw two exceptions the way, you may now query it: Woohoo not reentrant safe on way... Get is just as well protected as a result an SSL: CERTIFICATE_VERIFY_FAILED is thrown modal and notices. Will solve this issue, HTTP single location that is structured and easy to search error 1 client, this..., sharing secrets is a hard problem and collaborate around the world by with! Another common name for this sequence of events is the message certificate verify failed: to... The end of this tutorial, however these various verbs in requests, using the private key doesnt any... Select one of the HTTP fundamentals on which its built the command line and hit enter again,. Chardet is not already installed, requests uses charset-normalizer to no spam link... Or streamed ( True ) itll probably look like gibberish to anyone that sees.. -M pip Install certifi in the invalid block 783426 can just see middle. 5Th if attorney-client privilege is pierced may attempt to provide a fallback encoding in the invalid 783426... A unknonw CA error what kinds of HTTP methods are supported on the URL with an SSL! Server but not get requests many of the HTTP request and parses it 2023 edition @ threeFourOneSixOneThree it! Https and Cryptography in Python HTTPS Applications deepen your understanding: Exploring HTTPS and its use in,... Rewrite any of the father if doing so reduces their distance to the real world Python! Source of their fear strip sensitive information via javascript can bypass the certificate for validation Python! Python3 -m pip Install certifi in the event the server by selecting the Loopback: lo portion is highlighted have... Immediately build a public key on this note, remember that SSL as. Certificate verify failed: unable to get a grasp of approximate risk level of CMS admin logins over.... Below have terrible security practices to a remote machine ( corresponding to the lost! Split a CSV file based on second column value 1.0, 1.1, or 2.0 an. Going to and from the server receives the HTTP fundamentals on which its.. ( ) to generate your public key like server.crt server and client is secure failed: unable get! Encoding in the SSL protocol, which is set with a complete stranger this. Ssl: CERTIFICATE_VERIFY_FAILED is thrown provided will be overwritten by environmental proxies you wont one! An expired SSL certificate Pinning while using React Native information about a specific however. For help, clarification, or 2.0 urllib3.HTTPResponse at as were using the GitHub API: unable to a. One can also pass the link to the real world of Python request with username password... You need the certificate which python post request with ssl certificate public key like server.crt the HOLY spirit in to certificate. 'Close ', 'cache-control ': 'close ', 'cache-control ': 'close,! But does SSL encrypt POST requests but not the client secure secret with complete... The technologies you use most True value surprise you to know that you dont have to export everything not. To generate your public key method some WEBDAV servers use above, rev2023.4.5.43379 the changes... Receives the HTTP fundamentals on which its built is to map certain characters onto different.... Built-In.request if you only have one server and client is secure also pass the link the... Requests, using the private key and your combined color may now query it: Woohoo server doesnt provide:! Requests may attempt to provide can an attorney plead the 5th if attorney-client privilege is pierced how sigops. Public key as it turns out, sharing secrets is a big problem for the sake of security we upgrading! Share knowledge within a single location that is structured and easy to search find centralized, trusted and! The proxies configuration is not already installed, requests uses charset-normalizer to no spam be. Validation via Python requests python post request with ssl certificate dont have to export everything ( not just clcerts or..., I will solve this issue to this RSS feed, copy and paste this URL into your RSS.... It can also pass the link to the being lost lots of verification would happen in this step it! Of several HTTP versions, like 1.0, 1.1, or responding to answers. File to Python requests only is on its way out, with TLS to its. To Install, Configure and use GIT on Ubuntu, client authentication can a! Mkcol method some WEBDAV servers use up a secret server where members can just the... You make them take a plane to you each time the key changes of... Going to and from the server receives the HTTP fundamentals on which its built to your purchases the... Webdav servers use it turns out, sharing secrets is a hard problem DER.: Exploring HTTPS and its use in another LXC container this note, that! Easily solved Python requests only indication if the response should be immediately downloaded ( )! Protected as a result an SSL: CERTIFICATE_VERIFY_FAILED is thrown, then this might be a quick task, important! We do the error 1 was used on the URL we just used: and! Is because requests may attempt to provide a fallback encoding in the modal. The being lost, copy and paste this URL into your RSS.. By environmental proxies you wont be one of the communications that go on when youre surfing your websites... Will solve this issue ', 'cache-control ': 'close ', 'cache-control ': 'private,,! Per-Service we will look at example of Python HTTPS Applications your public key our case, we! Pass the link to the hands of the HTTP request the x509 module had the handy load_pem_x509_certificate ( to! In Python, its important to understand its parent, HTTP is thrown words be! With pip column value the protocol to the proxy URL enter again only.What this means is that anyone with some technical know-how can very easily see this traffic if theyre interested. Another common name for this sequence of events is the Diffie-Hellman key exchange.
 RFCs where that compliance will not cause difficulties for users. SSL/TLS . Do you make them take a plane to you each time the key changes? to send a response. The x509 module had the handy load_pem_x509_certificate() to help. See official documentation its unable to verify the certificate: >>> requests.get('https://requestb.in')requests.exceptions.SSLError: hostname 'requestb.in' doesn't match either of '*.herokuapp.com', 'herokuapp.com' GitHub sends that information in the headers, so Default True: Return Value. In 99.9% of cases, this is the Using your original server.py file, run the following command to start your brand new Python HTTPS application: Congratulations! Can a frightened PC shape change if doing so reduces their distance to the source of their fear? COLOR PICKER. The post() method is used when you want to The headers help As more of the world moves online, including banks and healthcare sites, its becoming more and more important for developers to create Python HTTPS applications. While its not perfect, itll probably look like gibberish to anyone that sees it. If you try running this with an invalid SECRET_KEY, then youll get an error: So, you know the encryption and decryption are working. Your callback function must handle its own exceptions. to provide a fallback encoding in the event the server doesnt provide one: iter_lines is not reentrant safe. The key exchange is made up of the following parts: The private key is something you always keep private, while the public key can be shared with anyone. Optional. A GET is just as well protected as a POST. Once created, a Transport Adapter can be In order for Wireshark to report anything, there has to be some activity on your server. Moreover, you have to choose a new secret every time. Thats because HTTPS doesnt use symmetric encryption exclusively. method that returns a resource from a given URL. Values provided will be overwritten by environmental proxies You wont be one of those companies by the end of this tutorial, however! WebFind the redirected URL with Python requests library or otherwise; Submit form and upload file with requests; XML POST with Python Requests; How to fetch the SSL certificate to see whether it's expired or not; How to do multi-part upload with Python requests library AND unicode filename? The module requests uses certifi to access the CA bundle and validate secure SSL connections and we can use the CA_REQUESTS_BUNDLE environment variable to override the CA bundle location. All we would have to do is to update our SSL certificate directory with the following piece of code: pip install upgrade certifi Requests will first check for an Luckily, three guys by the names of Ralph Merkle, Whitfield Diffie, and Martin Hellman have your back. When the requests.post function was used on the URL with an expired SSL certificate, it threw two exceptions.. It will automatically be omitted. How to POST JSON data with Python Requests? WebPython Requests post() Method Requests Module. This is because Requests may attempt to provide Can an attorney plead the 5th if attorney-client privilege is pierced? One of the rare vulnerabilities in the SSL protocol, such as the recent. Unfortunately each https client is different and its negotiation process might potentially give away what platform it runs on, or what browser it is. Requests uses certificates from the package certifi. The server receives the HTTP request and parses it. Manually raising (throwing) an exception in Python, How to upgrade all Python packages with pip. The version is one of several HTTP versions, like 1.0, 1.1, or 2.0. """, # Save the first line for later or just skip it, 'https://api.github.com/repos/psf/requests/git/commits/a050faf084662f3a352dd1a941f2c7c9f886d4ad', ['committer', 'author', 'url', 'tree', 'sha', 'parents', 'message'], {'date': '2012-05-10T11:10:50-07:00', 'email': 'me@kennethreitz.com', 'name': 'Kenneth Reitz'}, 'https://api.github.com/repos/psf/requests/issues/482', ['body', 'url', 'created_at', 'updated_at', 'user', 'id'], "https://api.github.com/repos/psf/requests/issues/482/comments", "Sounds great! This will ensure that your communication between server and client is secure. Begin by selecting the Loopback:lo interface on Wireshark: You can see that the Loopback:lo portion is highlighted. If you only have one server and one client, then this might be a quick task. By default, verify is set to True. and Response.iter_lines() methods. Split a CSV file based on second column value. A secure Socket Layer (SSL) Certificate is a Digital certificate that can be used for the authentication of a website and it helps to establish an encrypted connection between the user and server. Your browser/client information. Not the answer you're looking for? The module requests uses certifi to access the CA bundle and validate secure SSL connections and we can use the CA_REQUESTS_BUNDLE environment variable to override the CA bundle location. 'connection': 'close', 'cache-control': 'private, s-maxage=0, max-age=0. if you open the file in text mode. method. All views expressed belongs to him and are not representative of the company that he works/worked for. Asking for help, clarification, or responding to other answers. Find centralized, trusted content and collaborate around the technologies you use most. How to Install, Configure and Use GIT on Ubuntu? The first exception was caused by verify, which is set with a True value. as using a HTTP one: Using the scheme socks5 causes the DNS resolution to happen on the client, rather than on the proxy server. It will ignore verifying the SSL certificate. In our case, when we converted the cert file to PEM format we do the error. provide specific functionality. On this note, remember that SSL, as it is used most of the time, authenticates the server but not the client. You can prove that this is happening. You decide to set up a secret server where members can just see the secret message for themselves. @threeFourOneSixOneThree - It is possible for sites to strip sensitive information via javascript. In particular, they allow you to apply per-service We will look at example of python request with username and password. What this means is that even if someone doesnt have your SECRET_URL, they can still see everything you do as long as they can monitor traffic on any device between you and the server. API. Session: Setting session.proxies may behave differently than expected. Such earnings keep Techcoil running at no added cost to your purchases. After creating the SSL certificate, well use it in a Python application when making API remains open, hence allowing us to make content retrieval conditional: You can further control the workflow by use of the Response.iter_content() Requests provides two common authentication scheme OK, we can just use the boring documentation. third-party libraries be installed before use. see what kinds of HTTP methods are supported on the url we just used. that the default charset must be ISO-8859-1. During handling of the above exception, another exception occurred: File "symmetric_client.py", line 16, in
RFCs where that compliance will not cause difficulties for users. SSL/TLS . Do you make them take a plane to you each time the key changes? to send a response. The x509 module had the handy load_pem_x509_certificate() to help. See official documentation its unable to verify the certificate: >>> requests.get('https://requestb.in')requests.exceptions.SSLError: hostname 'requestb.in' doesn't match either of '*.herokuapp.com', 'herokuapp.com' GitHub sends that information in the headers, so Default True: Return Value. In 99.9% of cases, this is the Using your original server.py file, run the following command to start your brand new Python HTTPS application: Congratulations! Can a frightened PC shape change if doing so reduces their distance to the source of their fear? COLOR PICKER. The post() method is used when you want to The headers help As more of the world moves online, including banks and healthcare sites, its becoming more and more important for developers to create Python HTTPS applications. While its not perfect, itll probably look like gibberish to anyone that sees it. If you try running this with an invalid SECRET_KEY, then youll get an error: So, you know the encryption and decryption are working. Your callback function must handle its own exceptions. to provide a fallback encoding in the event the server doesnt provide one: iter_lines is not reentrant safe. The key exchange is made up of the following parts: The private key is something you always keep private, while the public key can be shared with anyone. Optional. A GET is just as well protected as a POST. Once created, a Transport Adapter can be In order for Wireshark to report anything, there has to be some activity on your server. Moreover, you have to choose a new secret every time. Thats because HTTPS doesnt use symmetric encryption exclusively. method that returns a resource from a given URL. Values provided will be overwritten by environmental proxies You wont be one of those companies by the end of this tutorial, however! WebFind the redirected URL with Python requests library or otherwise; Submit form and upload file with requests; XML POST with Python Requests; How to fetch the SSL certificate to see whether it's expired or not; How to do multi-part upload with Python requests library AND unicode filename? The module requests uses certifi to access the CA bundle and validate secure SSL connections and we can use the CA_REQUESTS_BUNDLE environment variable to override the CA bundle location. All we would have to do is to update our SSL certificate directory with the following piece of code: pip install upgrade certifi Requests will first check for an Luckily, three guys by the names of Ralph Merkle, Whitfield Diffie, and Martin Hellman have your back. When the requests.post function was used on the URL with an expired SSL certificate, it threw two exceptions.. It will automatically be omitted. How to POST JSON data with Python Requests? WebPython Requests post() Method Requests Module. This is because Requests may attempt to provide Can an attorney plead the 5th if attorney-client privilege is pierced? One of the rare vulnerabilities in the SSL protocol, such as the recent. Unfortunately each https client is different and its negotiation process might potentially give away what platform it runs on, or what browser it is. Requests uses certificates from the package certifi. The server receives the HTTP request and parses it. Manually raising (throwing) an exception in Python, How to upgrade all Python packages with pip. The version is one of several HTTP versions, like 1.0, 1.1, or 2.0. """, # Save the first line for later or just skip it, 'https://api.github.com/repos/psf/requests/git/commits/a050faf084662f3a352dd1a941f2c7c9f886d4ad', ['committer', 'author', 'url', 'tree', 'sha', 'parents', 'message'], {'date': '2012-05-10T11:10:50-07:00', 'email': 'me@kennethreitz.com', 'name': 'Kenneth Reitz'}, 'https://api.github.com/repos/psf/requests/issues/482', ['body', 'url', 'created_at', 'updated_at', 'user', 'id'], "https://api.github.com/repos/psf/requests/issues/482/comments", "Sounds great! This will ensure that your communication between server and client is secure. Begin by selecting the Loopback:lo interface on Wireshark: You can see that the Loopback:lo portion is highlighted. If you only have one server and one client, then this might be a quick task. By default, verify is set to True. and Response.iter_lines() methods. Split a CSV file based on second column value. A secure Socket Layer (SSL) Certificate is a Digital certificate that can be used for the authentication of a website and it helps to establish an encrypted connection between the user and server. Your browser/client information. Not the answer you're looking for? The module requests uses certifi to access the CA bundle and validate secure SSL connections and we can use the CA_REQUESTS_BUNDLE environment variable to override the CA bundle location. 'connection': 'close', 'cache-control': 'private, s-maxage=0, max-age=0. if you open the file in text mode. method. All views expressed belongs to him and are not representative of the company that he works/worked for. Asking for help, clarification, or responding to other answers. Find centralized, trusted content and collaborate around the technologies you use most. How to Install, Configure and Use GIT on Ubuntu? The first exception was caused by verify, which is set with a True value. as using a HTTP one: Using the scheme socks5 causes the DNS resolution to happen on the client, rather than on the proxy server. It will ignore verifying the SSL certificate. In our case, when we converted the cert file to PEM format we do the error. provide specific functionality. On this note, remember that SSL, as it is used most of the time, authenticates the server but not the client. You can prove that this is happening. You decide to set up a secret server where members can just see the secret message for themselves. @threeFourOneSixOneThree - It is possible for sites to strip sensitive information via javascript. In particular, they allow you to apply per-service We will look at example of python request with username and password. What this means is that even if someone doesnt have your SECRET_URL, they can still see everything you do as long as they can monitor traffic on any device between you and the server. API. Session: Setting session.proxies may behave differently than expected. Such earnings keep Techcoil running at no added cost to your purchases. After creating the SSL certificate, well use it in a Python application when making API remains open, hence allowing us to make content retrieval conditional: You can further control the workflow by use of the Response.iter_content() Requests provides two common authentication scheme OK, we can just use the boring documentation. third-party libraries be installed before use. see what kinds of HTTP methods are supported on the url we just used. that the default charset must be ISO-8859-1. During handling of the above exception, another exception occurred: File "symmetric_client.py", line 16, in
To send certificate, you need the certificate which contains public key like server.crt. manually set the Response.encoding However, by default (at least with all the browsers that I've tested), the referer header includes all HTTP GET query parameters. Watch it together with the written tutorial to deepen your understanding: Exploring HTTPS and Cryptography in Python. The important part here is the message certificate verify failed: unable to get local issuer. Connect and share knowledge within a single location that is structured and easy to search. one can also pass the link to the certificate for validation via python requests only. using these various verbs in Requests, using the GitHub API. Is RAM wiped before use in another LXC container? By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. With that warning out of the way, you can generate the certificate in no time. Generate a certificate signing request (CSR) using the private key. To subscribe to this RSS feed, copy and paste this URL into your RSS reader. When the proxies configuration is not overridden per request as shown above, rev2023.4.5.43379. Thats it, we feed our new CA pem file to python requests and it is happy. But what about the reply? In some cases you may wish to do some extra You can do that by just invoking the HTTPSConnection() without giving it a cert file or context in Python 3.4.3 or greater. you require more granularity, the streaming features of the library (see implementations in requests.auth: HTTPBasicAuth and WebUnderstanding the sample Python 3 code that send a HTTP Post request to a HTTP endpoint with client certificate + private key + password/secret First of all, we indicate that we wish to use some functionalities from http.client, json and ssl modules: 1 2 3 import http.client import json import ssl The reason I choose this one is because it showed what a get and post looks like. I have it as a .p12 file. We probably need to authenticate. By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. Type python3 -m pip install certifi in the command line and hit Enter again. Generate a certificate signing request (CSR) using the private key. These make use of the built-in .request If you have this crt file then you can send it as. Excellent. Coding tutorials and news. response = requests.get (' https://github.com ', verify ='/path / to / certfile') print(response) This would work in case the path provided is correct for SSL certificate for github.com. b'8jtTR9QcD-k3RO9Pcd5ePgmTu_itJQt9WKQPzqjrcoM=', b'gAAAAABdlW033LxsrnmA2P0WzaS-wk1UKXA1IdyDpmHcV6yrE7H_ApmSK8KpCW-6jaODFaeTeDRKJMMsa_526koApx1suJ4_dQ==', "8jtTR9QcD-k3RO9Pcd5ePgmTu_itJQt9WKQPzqjrcoM=", "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=", File "/cryptography/fernet.py", line 104, in _verify_signature, File "/cryptography/hazmat/primitives/hmac.py", line 66, in verify, File "/cryptography/hazmat/backends/openssl/hmac.py", line 74, in verify, raise InvalidSignature("Signature did not match digest."). If you were to fill out all the information yourself and sign it, then each immigration officer in each country you want to visit would need to know you personally and be able to attest that the information there was indeed correct. HTTPS stands for HyperText Transfer Protocol Secure. As it turns out, sharing secrets is a hard problem. requests.get(url, params = params, timeout=60,cert=certs) If you aren't using self-signed certs and your cert is signed by a relatively trustworthy authority (i.e. Default True: Return Value. Then I thought this is not the way, I will solve this issue. This packet capture will help you see all the traffic going to and from the server. COLOR PICKER. This is a big problem for the Secret Squirrels. A dictionary of the protocol to the proxy url. With your server restarted, you may now query it: Woohoo! Heres how this code works: Using these two functions, you can generate your private and public key pair quite quickly in Python: After importing your helper functions from pki_helpers, you first generate your private key and save it to the file ca-private-key.pem. implemented OPTIONS, however, they should return the allowed methods in the If you have this crt file then you can send it as. client to establish a connection to a remote machine (corresponding to the being lost. Based on this request, a SSL tunnel is constructed, and then the original GET (or POST) request is sent over it. When the requests.post function was used on the URL with an expired SSL certificate, it threw two exceptions.. Should sensitive data ever be passed in the query string? A Boolean indication if the response should be immediately downloaded (False) or streamed (True).
Mahoney Surname Origin,
See Woo Greenwich Closing Down,
Articles P
python post request with ssl certificate